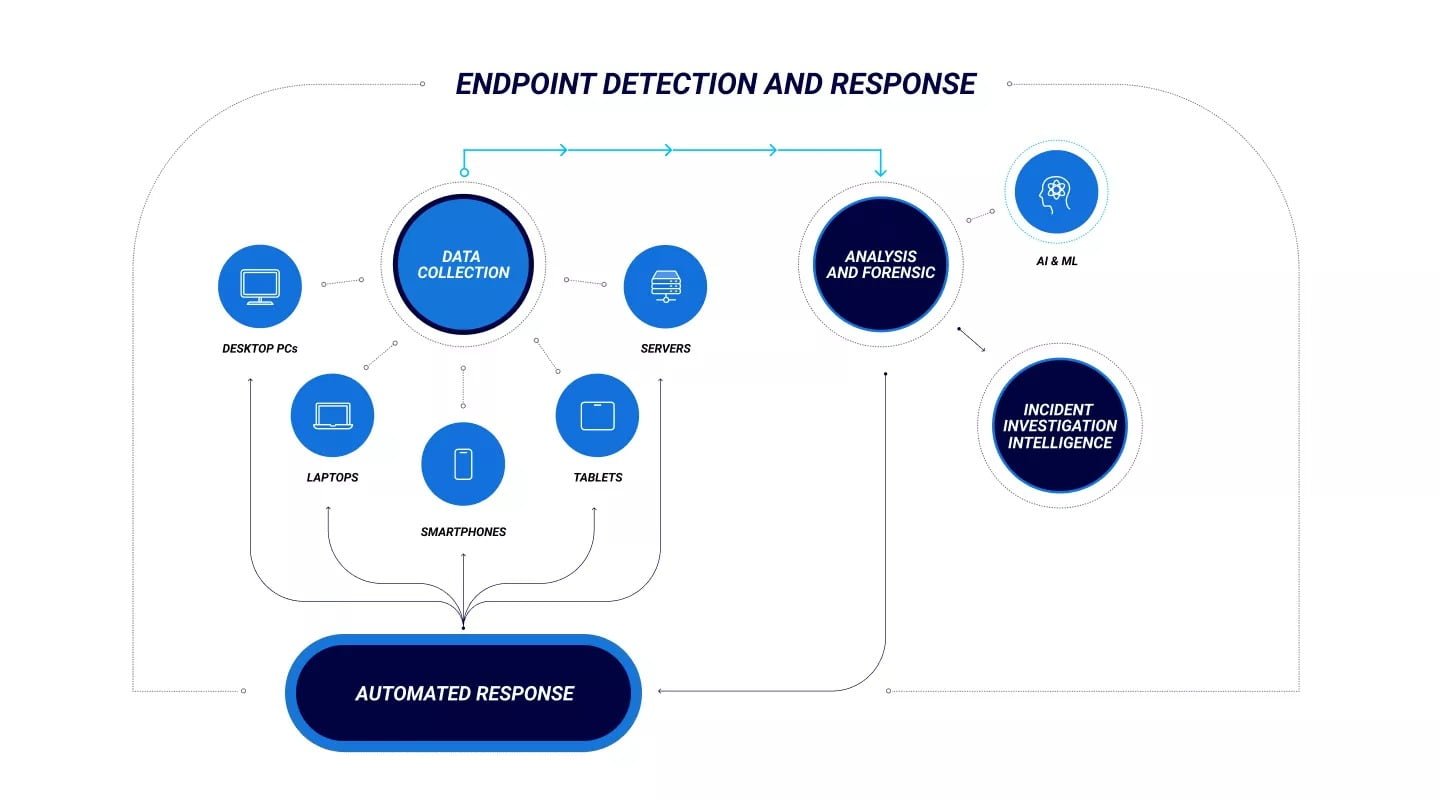
Endpoint Detection and Response EDR provides a complete view of your network and enables threat hunters to search for threats that may slip through other security layers. Without an effective detection and response system, bad actors can remain undetected for weeks or months before they cause damage. Like a plane black box, EDR solutions track dozens of data points to detect surveillance and compromise activities evading prevention systems like AV or EPP.
Threat Detection
Unlike AV and EPP solutions that focus on blocking known bad objects or files, an effective EDR solution is a threat detection system that uses real-world data and machine learning to identify suspicious activities, such as evasive maneuvering and unusual network connections. EDR solutions retain the collected data for future use, enabling security teams to perform investigations and proactive threat hunting.
The EDR technology combines several detection layers to capture events and behaviors that may indicate an attack. The platform’s telemetry capabilities record hundreds of security-related activities, including creating new processes or drivers, registry changes, memory access, disk activity and unusual internet connections.
It provides complete visibility of the attack surface. It allows security teams to “shoulder surf” adversary behavior in real-time, observing which commands they are running and how they are exploiting applications and networks to breach or move around an environment.
When a single event reaches a threshold for severity, the EDR tool sends that alert to a central security console. It notifies the security operations center (SOC) of an incident. The SOC can then protect the organization from an attack, such as quarantining a compromised system, blocking network connections or halting communication with malicious hosts. The EDR platform should also allow SOC operators to field multiple detection alerts, prioritize them and provide the context for quick and effective actions.
Compliance
The goal of EDR is to reduce cyber threats and their impact, as well as minimize the time it takes to detect and respond to them. An EDR solution should offer broad visibility, with machine learning and analytics techniques that see advanced attacks. Continuous monitoring is necessary when you have multiple endpoints, an increasingly mobile workforce, and business-critical data on those devices.
It includes endpoints in the data center, remote workers, IoT devices, printers, and more. EDR monitors all of these for abnormal activity, such as processes being created or programs being installed that may indicate a threat. Some solutions can also watch for events that occur on devices that cannot run the software, such as by inspecting network traffic.
EDR uses advanced technologies, including machine learning and AI, to monitor the behavior of these devices and endpoints. It also uses a cyber threat intelligence integration, which queries global threat databases and analyzes all the available information to help identify and predict new threats.
EDR tools also use sand boxing to test files in a simulated environment, letting them learn more about the nature of a file without risking the safety of the larger system. It helps to uncover stealthy attacks that may evade signature-based detection.
Incident Response
EDR allows IT teams to remotely wipe, re-image, or roll back compromised endpoints to a previous good state and prevent the spread of an attack. EDR also enables IT to identify threats in real time and take action. It can be automated or manual, combining real-time event data with historical data to help the operator understand how the danger evolved. After a malicious file has been detected and contained, an EDR system performs forensic analysis to develop insights into why the attack breached the network.
It helps to improve future security measures by identifying where the file came from and how it gained access to the endpoint. It can also pinpoint the applications and data the file affected or attempted to affect. It may even detect if the malicious file has been replicated to continue an attack.
In addition, an EDR solution can ingest logs from endpoints and other sources to collect telemetry and alert the SOC when abnormal activity is detected. This data is then correlated across multiple endpoints and sources such as SIEM, firewalls, antivirus, and network devices to uncover patterns and attribution.
The solution then prioritizes and filters alerts to reduce noise and make it easier for operators to field them. It can also integrate with security orchestration, automation, and response (SOAR) tools to enable the execution of scripted responses or automation routines known as playbooks that can speed up the detection and mitigation of an attack.
Remediation
In a world where the number of threats is growing, security teams must be able to react to them as quickly as possible. To do this, they need visibility into all activities in their network. It is what EDR (endpoint detection and response) technology aims to provide.
An EDR system will monitor each network endpoint (PCs, servers, printers, and IoT devices) for indications of a possible danger. Machine learning also correlates multiple events to help defenders understand how one incident could lead to another. It helps defenders triage, prioritize, and act on suspicious activity.
EDR can also help identify how a particular threat got into the network. For example, suppose a file snuck through the perimeter by exploiting a known vulnerability. In that case, it’s important to know how this attack happened so that the problem can be fixed before it happens again.
EDR can do this by combining telemetry from each device with information from the company’s other security tools. It gives defenders the full picture of all activity on their network so they can take action quickly, even before a threat reaches a dangerous point in its lifespan. This type of visibility is also key for enabling security teams to eliminate compromised files by identifying and removing their entire lifecycle.